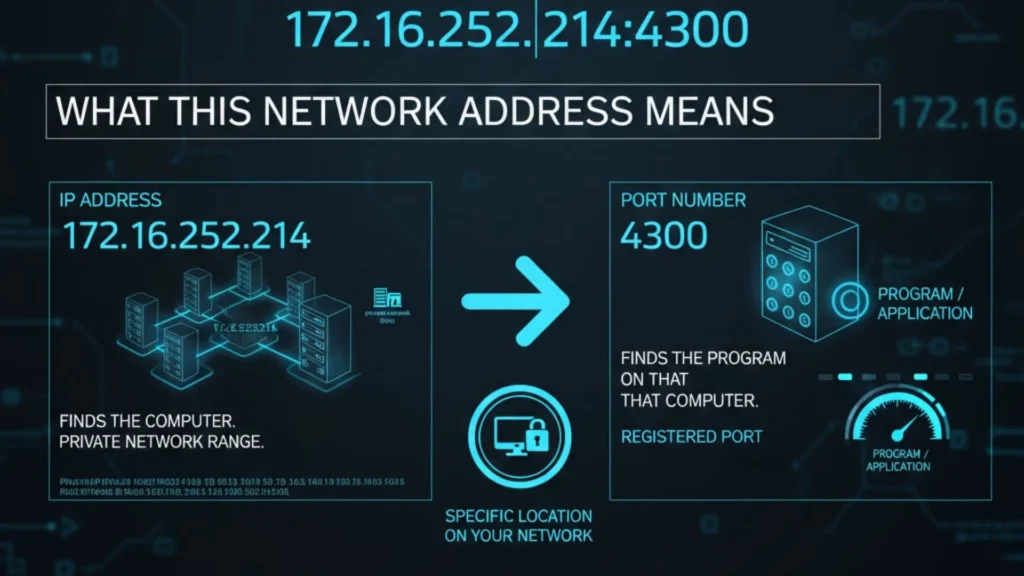
172.16.252.214;4300: What This Private IP Address and Port Mean
You see 172.16.252.214;4300 in your network settings. What is it? It has two parts. First part: 172.16.252.214 – This is an IP address. Second part: 4300 – This is a port number. Together, they point to one specific location on your network. The IP address finds the computer. The port finds the program on that computer.
Understanding the Private IP Address 172.16.252.214
Private Network Range
The address 172.16.252.214 is private. It only works inside your network. You cannot use it on the internet. Three ranges are private:
- 10.0.0.0 to 10.255.255.255.
- 172.16.0.0 to 172.31.255.255.
- 192.168.0.0 to 192.168.255.255.
Your 172.16.252.214;4300 sits in the second range. Companies pick from these ranges for internal devices.
Why Use Private Addresses?
Private IPs save money. You don’t buy public addresses for each device. They add protection. Hackers cannot reach them directly from outside. Many companies can use the same private addresses. They stay separate because they’re on different networks. You get full control over your addressing scheme.
Port 4300 Explained
Port Number Categories
Ports go from 0 to 65535. Three types exist: System ports run from 0 to 1023. Registered ports run from 1024 to 49151. Private ports run from 49152 to 65535. Port 4300 is registered.
Common Uses for Port 4300
Your company decides what runs on 172.16.252.214;4300. Some examples:
- Internal web apps.
- Database servers.
- Custom software.
- Testing servers.
- File servers.
- Monitoring systems.
No standard says “port 4300 must be X.” Different companies use it differently.
Real-World Applications of 172.16.252.214;4300
Enterprise Environments
Big companies use 172.16.252.214;4300 for internal tools. Your HR system might run here. Employees check their payslips and vacation days. Your inventory system could use this address. Warehouse staff track products coming and going. Customer service might access their ticketing system here.
Development and Testing
Programmers set up test servers at addresses like 172.16.252.214;4300. They build new features. They test everything before going live. Breaking things here doesn’t hurt real users. This setup keeps experiments separate from production.
Database Connections
Databases often run on special ports. Using 172.16.252.214;4300 for your database hides it better. Attackers scan common ports first. They check 3306 for MySQL. They check 5432 for PostgreSQL. Your database on port 4300 gets less attention.
Connecting to 172.16.252.214;4300
Basic Requirements
Three things let you connect to 172.16.252.214;4300: You must be on the same network. Firewalls must allow your connection. You need the right software.
Connection Methods
Browser: Type http://172.16.252.214: 4300 in the address bar. Command line: Open terminal and type commands. Apps: Enter the address in your program settings. Testing tools: Use Postman or similar apps. Most systems want a colon not a semicolon. Write it as 172.16.252.214:4300 normally.
Troubleshooting Connection Problems
Testing Connectivity
First, check if the computer is on. Type this:
ping 172.16.252.214You see replies if it’s working. Next, check the port. Type this:
telnet 172.16.252.214 4300Connection means the service is running.
Common Issues
Cannot connect – The service stopped or never started. Check if someone turned it off. Takes too long – Firewall blocks you or network routing broke. Check your firewall settings. Cannot find host – The computer is off or the address is wrong. Verify the IP address. Login fails – Your username or password is wrong. Get the right credentials from your admin.
Security Best Practices
Access Control
Not everyone needs 172.16.252.214;4300 access. Block most people. Allow only those who need it. Set firewall rules by department. A sale needs different access than accounting. Put sensitive systems on separate networks.
Encryption and Authentication
Turn on HTTPS if possible. Encrypted data stays safe during transfer. Make strong passwords:
- At least 12 letters and numbers.
- Mix capitals and lowercase.
- Add special characters.
Use two-factor codes when you can.
Monitoring and Logging
Watch who connects to 172.16.252.214;4300.Your logs show:
- User names
- Connection times
- Actions taken
- Errors
Someone trying the wrong passwords five times needs checking.
Set alerts for weird activity.
Network Configuration
Firewall Rules
Write rules for 172.16.252.214;4300:
Let through:
- From: Your office computers
- To: 172.16.252.214
- Port: 4300
- Do: Allow
Block:
- From: Everyone else
- To: 172.16.252.214
- Port: 4300
- Do: Deny
First rules run first. Put specific rules before general ones.
Router Configuration
Routers move traffic to 172.16.252.214;4300. Add routes so data finds its way. Some networks need NAT rules. Write down all changes you make.
Load Balancing
Several servers can answer at 172.16.252.214;4300. A load balancer spreads work between them. One server dies? Traffic goes to the others automatically. Check servers every minute to catch failures fast.
Documentation Requirements
Essential Information
Write down facts about 172.16.252.214;4300:
- What program runs here
- Who owns it
- What it needs to work
- How to fix it
- When you do maintenance
Update notes when things change. Old information wastes time during emergencies.
Performance Monitoring
Key Metrics
Watch these numbers for 172.16.252.214;4300:
Up or down: Does it respond? Speed: How fast does it answer? Errors: How many requests fail? Volume: How much data moves through? Set limits for each number. Get alerts when something goes wrong.
Capacity Planning
Check how busy your system gets. Watch processor and memory use each week. Add more resources before you run out. Growth patterns tell you when to upgrade.
Conclusion
172.16.252.214;4300 is a network endpoint combining a private IP with a port number. The private address keeps systems hidden from the internet. The port separates different programs on one computer. Set firewalls to block unauthorized users. Use encryption for data protection. Monitor connections daily. Document every change you make. Test updates before deploying them. Keep logs for security reviews. This setup works for internal business systems that need protection and reliability.







